# Securing HPE Ezmeral Container Platform using Sysdig Secure and Sysdig Monitor
To address the security challenges that exist in containerized environments, this solution leverages the Sysdig SaaS Platform to secure and monitor the HPE Ezmeral Container Platform, an enterprise-ready Kubernetes platform that is installed and configured on HPE Synergy Composable Infrastructure. After the HPE Ezmeral Container Platform Kubernetes cluster is deployed, cluster access is granted to the Sysdig SaaS Platform. The Sysdig SaaS Platform is a cloud-based service where the security and monitoring services will be available to the user based on the choice of subscription. For security and monitoring of HPE Ezmeral Container Platform containers, it is required to install the Sysdig Agent on the Kubernetes cluster. This means Sysdig Agents that are lightweight entities will be installed within each node in the HPE Ezmeral Container Platform Kubernetes cluster. These agents run as a daemon to enable Sysdig Monitor and Sysdig Secure functionality.
Sysdig Monitor provides deep, process-level visibility into dynamic, distributed production environment. Sysdig Secure provides image scanning, run-time protection, and forensics to identify vulnerabilities, block threats, enforce compliance, and audit activity across the Kubernetes cluster.
The key security benefits are:
Faster incident resolution using Sysdig Monitor for the cluster.
Simplified compliance for the entire solution.
Service-based access control for container security and monitoring.
Less time spent on managing platforms, containers, and vulnerabilities.
The implementation of Sysdig in this solution uses the Software as a Service (SaaS) deployment method. The playbooks deploy Sysdig Agent software to capture the data from every node in the HPE Ezmeral Container Platform Kubernetes deployment and the captured data is relayed back to your Sysdig SaaS Cloud portal. The deployment provides access to a 90-day try-and-buy, fully featured version of the Sysdig software. For more information about Sysdig agent deployment, see the HPE solutions for the HPE Ezmeral Container Platform GitHub at https://github.com/HewlettPackard/hpe-solutions-hpecp (opens new window)
for configuring Sysdig for HPE Ezmeral Container Platform
To install the Sysdig agents in an automated way, use the repository located at https://github.com/HewlettPackard/hpe-solutions-hpecp (opens new window). The folder scripts/security/sysdig within this repository contains the following:
Playbooks: This folder contains the playbooks required for Sysdig agent installation.
Roles: This folder contains a role called "sysdig-agent-deploy-hpecp" which is responsible for performing the actions required for Sysdig agent integration.
Hosts: This is the inventory file that will be used by the installer VM to reference hosts during Sysdig agent deployment. Provide the installer VM or the server which can access the Kubernetes cluster.
Figure 64 shows an overview of the steps involved in configuring
composer security via the automation.
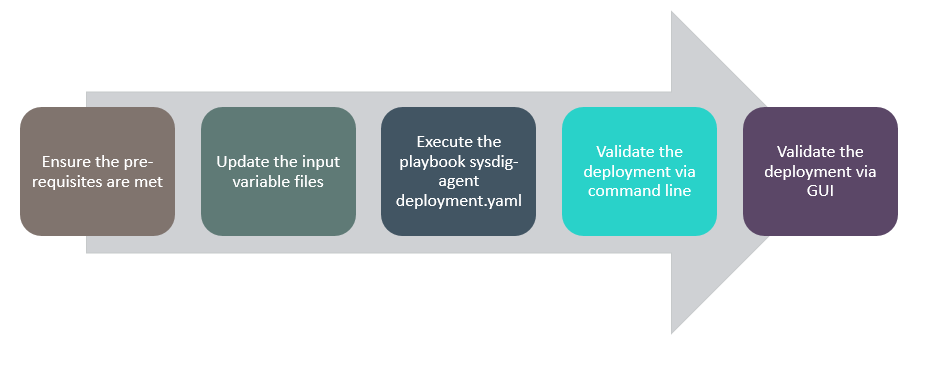 Figure 64. Flow of execution for composer security
Figure 64. Flow of execution for composer security
PREREQUISITES
To successfully deploy Sysdig agents on the nodes, the following prerequisites must be met:
HPE Ezmeral Container Platform Kubernetes cluster is up and running.
The installation user has SaaS-based access to Sysdig Secure and Sysdig Monitor for the purpose of container security.
The installation user has admin privileges for Sysdig Secure and Sysdig Monitor.
Sysdig agents with latest version deployed on HPE Ezmeral Container Platform.
The installation user has a valid access token that is given by Sysdig and is specific to their credentials on Sysdig Monitor and Sysdig Secure.
# Custom attributes or variable files and plays
Each playbook has a role associated with it. Each role has a set of tasks under the "task" folder and variables under the "var" folder. These variable values must be defined by the installation user according to the installation environment before running the plays:
roles/sysdig-agent-deploy-hpecp/vars/main.yml: Used during Sysdig agent deployment to HPE Ezmeral Container Platform Kubernetes cluster. This file contains Sysdig-related variables.
sysdig-agent-deploy-hpecp/tasks/main.yml: This file contains the actual Sysdig agent installation steps.
sysdig-agent-deploy-hpecp/files/sysdig-agent-configmap.yaml: This file is provided by Sysdig and handles the Sysdig software related configuration.
roles/sysdig-agent-deploy-hpecp/files/sysdig-agent-daemonset-v2.yaml: This file is provided by Sysdig and handles the Sysdig daemon related configuration.
# Executing the playbooks
This section describes the steps that need to be performed to use the playbooks:
Login to the installer VM.
Browse the cloned directory and navigate to the following sub-directory.
> cd $BASE_DIR/security/sysdigNOTE
$BASE_DIR is defined and set in Installer machine section within this document.
Update the variables in the following files.
Provide the Installer VM or the server which has access to the HPE Ezmeral Container Platform Kubernetes cluster [master].
Edit the file /roles/sysdig-agent-deploy-hpecp/vars/main.yml.
Provide a value for the namespace for the Sysdig integration with HPE Ezmeral Container Platform under the "namespace" variable.
Provide the Sysdig access key or token value. This value is retrieved from the user setting by logging into Sysdig Secure or Sysdig Monitor GUI in "accesskeyval" variable.
Edit the file /roles/sysdig-agent-deploy-hpecp/files/sysdig-agent-configmap.yaml.
Enter the Sysdig Collector address and port. Check with Sysdig about which collector is accessible in the installation environment and over which port.
Hewlett Packard Enterprise recommends access of Sysdig collector over Secure Socket Layer (SSL) port. For both the "ssl" and "ssl certificate validate" keys, set the value as "true".
-Set the variable related to the underlying Kubernetes deployment to true.
- Enter the cluster name of the Kubernetes cluster.
Run the play using following command.
> ansible-playbook -i hosts playbooks/sysdig-agent-deployment.yamlTo verify the deployment, login to the server which has access to the Kubernetes cluster and execute the following command.
> kubectl get all -n sysdig-agentThe output of this command displays the Sysdig agent names running on each of the nodes within the HPE Ezmeral Container Platform Kubernetes cluster. If you see a pod with a pending status, then there might be a possibility that the underlying HPE Ezmeral Container Platform worker node is not functional.
Figure 65 depicts the Sysdig agents running on HPE Ezmeral Container Platform Kubernetes nodes.
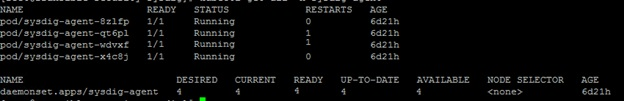 Figure 65. Sysdig agents running on Kubernetes nodes
Figure 65. Sysdig agents running on Kubernetes nodesLogin to Sysdig Secure web interface at https://sysdig.com/ as a user with administrative privileges.
From the Sysdig Secure web interface, click the icon named POLICY EVENTS and you will see the web interface for Policy Events tab. On the Policy Events tab, click the Groupings drop-down list and select Entire Infrastructure. The user with administrative privileges should be able to see all the cluster nodes.
Figure 66 depicts the HPE Ezmeral Container Platform Kubernetes cluster in Sysdig Secure.
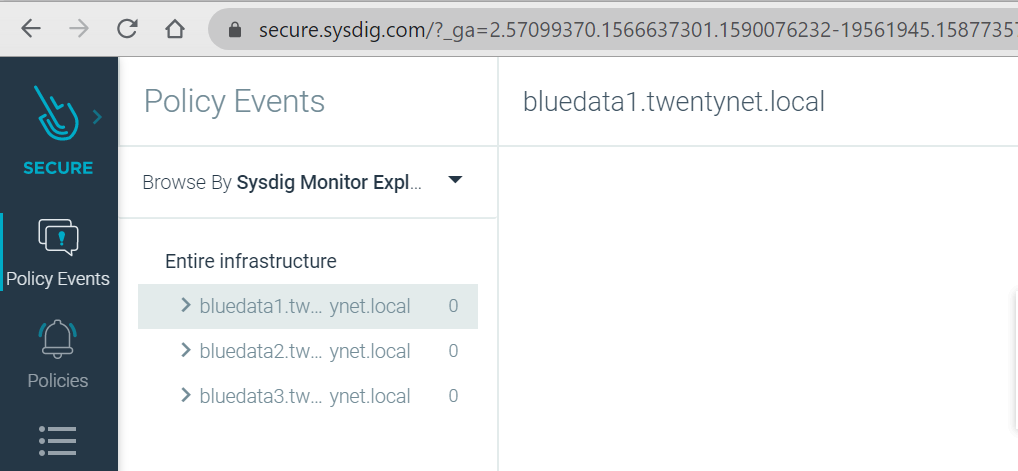 Figure 66. HPECP Kubernetes cluster in Sysdig Secure.
Figure 66. HPECP Kubernetes cluster in Sysdig Secure.From the Sysdig Monitor web interface, click Explore icon and you will see the web interface for the Explore tab. On the Explore tab, click the Data Source (two rectangles) drop-down menu and select the data source named Sysdig Agents from the drop-down list.
Open the Groupings drop-down list and select Clusters and Nodes. The user with administrative privileges should be able to see all the HPE Container Platform Kubernetes nodes.
Figure 67 depicts the HPE Ezmeral Container Platform Kubernetes cluster in Sysdig Monitor.
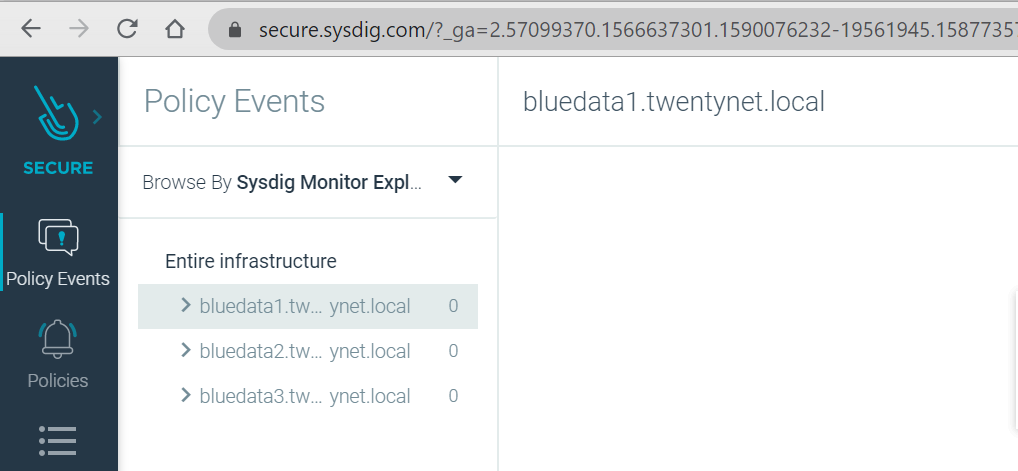 Figure 67. HPE Ezmeral Container Platform Kubernetes cluster in Sysdig
Monitor
Figure 67. HPE Ezmeral Container Platform Kubernetes cluster in Sysdig
MonitorNOTE
For an explanation of host requirements for agent installation, see https://docs.sysdig.com/en/host-requirements-for-agent-installation.html (opens new window).
It is recommended to use port 6443 to transfer data over Secure Socket Layer/ Transport Layer Security (SSL/TLS) protocol. Sysdig agents transfer data to Sysdig Cloud over HTTPS that encrypts and decrypts the requests and the responses returned by the Sysdig Cloud.
From the Sysdig Monitor web interface, click the EXPLORE icon. On the Explore tab, click the Data Source (two rectangles) drop-down menu and select the data source named Sysdig Agentsfrom the drop-down list. Open the Groupings drop-down list and select Deployment and Pods. A user with administrative privileges should be able to see all the agents and their details.
Figure 68 depicts the Sysdig agents running on HPE Ezmeral Container Platform Kubernetes cluster.
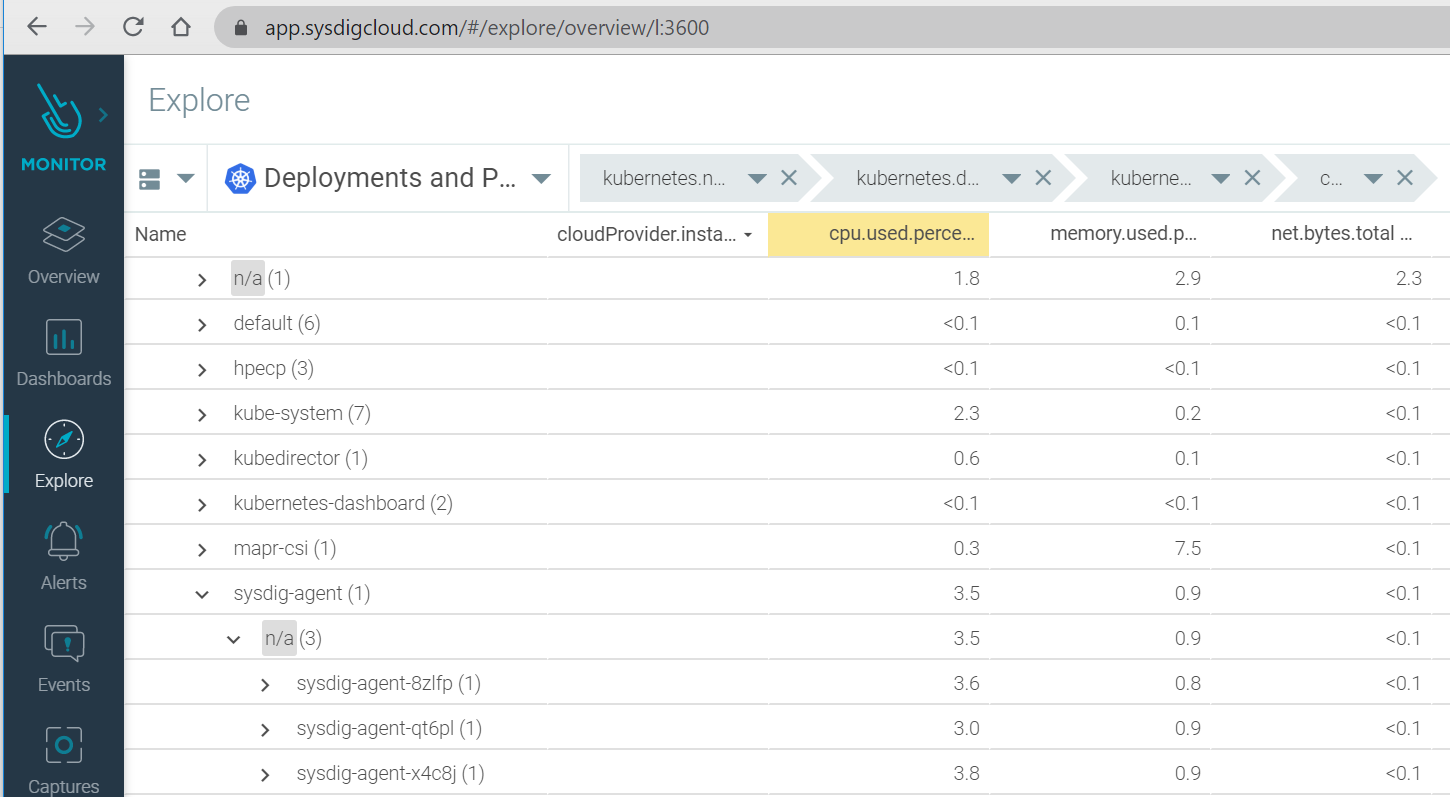 Figure 68. Sysdig agents running on HPE Container Platform Kubernetes
cluster
Figure 68. Sysdig agents running on HPE Container Platform Kubernetes
cluster