# HPECP Cluster Integration with Nimble
The HPE CSI(Container Storage Interface) Driver for Kubernetes allows user to use a Container Storage Provider (opens new window) (CSP) to perform data management operations on storage resources. We will be using Nimbule as a backend storage to perform the data Management Operation for the individual Kubernets cluster.
Installing the CSI Drivers
These object configuration files are common for version of Kubernetes.
- Worker node IO settings.
kubectl create -f https://raw.githubusercontent.com/hpe-storage/co-deployments/master/yaml/csi-driver/v1.3.0/hpe-linux-config.yaml (opens new window)
- Container Storage Provider:
kubectl create -f https://raw.githubusercontent.com/hpe-storage/co-deployments/master/yaml/csi-driver/v1.3.0/nimble-csp.yaml (opens new window)
- Kubernetes 1.18
kubectl create -f https://raw.githubusercontent.com/hpe-storage/co-deployments/master/yaml/csi-driver/v1.3.0/hpe-csi-k8s-1.18.yaml (opens new window)
Adding HPE Storage Backend
Once the CSI driver is deployed, two additional objects needs to be created to get started with dynamic provisioning of persistent storage, a Secret and a StorageClass.
Secret parameters
All parameters are mandatory and described below.
| Parameter | Description |
|---|---|
| serviceName | This hostname or IP address where the Container Storage Provider (CSP) is running, usually a Kubernetes Service, such as "nimble-csp-svc" or "primera3par-csp-svc" |
| servicePort | This is port the serviceName is listening to. |
| Backend | This is the management hostname or IP address of the actual backend storage system, such as a Nimble or 3PAR array. |
| username | Backend storage system username with the correct privileges to perform storage management. |
| password | Backend storage system password. |
1.Create the secret
custom-secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: custom-secret
namespace: kube-system
stringData:
serviceName: nimble-csp-svc
servicePort: "8080"
backend: 10.0.2.100
username: admin
password: admin
- Execute below command to create custom secret file
kubectl create -f custom-secret.yaml
We can see the secret in the “kube-system” Namespace
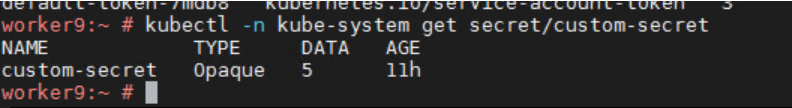
Create the StorageClass with the custome Secret
To use the new Secret "custom-secret", create a new StorageClass using the Secret and the necessary StorageClass parameters.
- Sample StorageClass.yaml file
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:
name: hpe-custom
provisioner: csi.hpe.com
parameters:
csi.storage.k8s.io/fstype: xfs
csi.storage.k8s.io/controller-expand-secret-name: custom-secret
csi.storage.k8s.io/controller-expand-secret-namespace: kube-system
csi.storage.k8s.io/controller-publish-secret-name: custom-secret
csi.storage.k8s.io/controller-publish-secret-namespace: kube-system
csi.storage.k8s.io/node-publish-secret-name: custom-secret
csi.storage.k8s.io/node-publish-secret-namespace: kube-system
csi.storage.k8s.io/node-stage-secret-name: custom-secret
csi.storage.k8s.io/node-stage-secret-namespace: kube-system
csi.storage.k8s.io/provisioner-secret-name: custom-secret
csi.storage.k8s.io/provisioner-secret-namespace: kube-system
description: "Volume created by using a custom Secret with the HPE CSI Driver for Kubernetes"
reclaimPolicy: Delete
allowVolumeExpansion: true
Run below command to create storage class.
kubectl create -f StorageClass.yaml
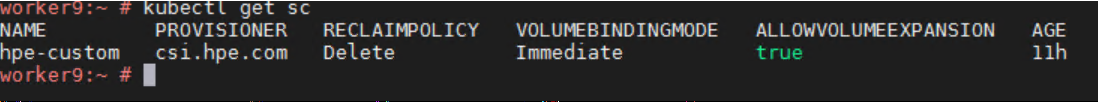
Create the PersistentVolumeClaim
Create a PersistentVolumeClaim. This object declaration ensures a PersistentVolume is created and provisioned.
PersistentVolumeClaim.yaml
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: my-first-pvc
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 32Gi
storageClassName: hpe-custom
kubectl create -f PersistentVolumeClaim.yaml
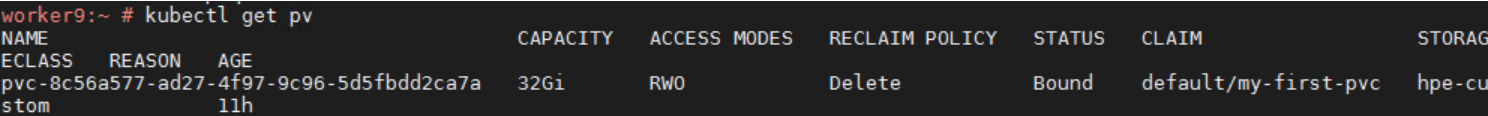
- Create the Pods
kind: Pod
apiVersion: v1
metadata:
name: my-pod
spec:
containers:
- name: pod-datelog-1
image: nginx
command: ["bin/sh"]
args: ["-c", "while true; do date >> /data/mydata.txt; sleep 1; done"]
volumeMounts:
- name: export1
mountPath: /data
- name: pod-datelog-2
image: debian
command: ["bin/sh"]
args: ["-c", "while true; do date >> /data/mydata.txt; sleep 1; done"]
volumeMounts:
- name: export1
mountPath: /data
volumes:
- name: export1
persistentVolumeClaim:
claimName: my-first-pvc
- Once the pods are deployment we can list the running pods.
kubectl get pods
`These pods will be using the above created pv’s for their data storage which reside on HPE Nimble Storage in the backend.