# HPE Ezmeral Container Platform - Role Based Access Control
Role-based access control (RBAC), also known as role-based security, is a framework that restricts system access. It does so, by setting permissions and privileges to enable access to authorized users. Most organizations use role-based access control to provide their employees with varying levels of access based on their roles and responsibilities. This protects sensitive data and ensures employees can only access information and perform actions they need to do their duties.
# Users and Roles in HPE Ezmeral Container Platform
The HPE Ezmeral Container Platform provides multi-tenant hybrid cloud platform. This multi-tenant platform is based on Role-based access control. Some of the user- and tenant-related considerations to be resolved when planning/maintaining your deployment include:
Tenants: The number of tenants and the function(s) each tenant performs will determine how many users with the Tenant Administrator role will be needed and, by extension, the number of users with the Tenant Member role will be needed for each tenant. The reverse is also true, since the number and functions of users needing to run jobs can influence how you define tenants. For example, different levels of confidentiality may mandate separate tenants.
Job functions: The specific work performed by a given user will directly impact the role they receive. For example, a small organization may designate a single user as the Tenant Administrator for multiple tenants, while a large organization may designate multiple Tenant Administrators per tenant.
Security clearances: You may need to restrict access to information based on a user's security clearance. This can impact both the tenant(s) a user has access to and the role configured for that user within a given tenant.
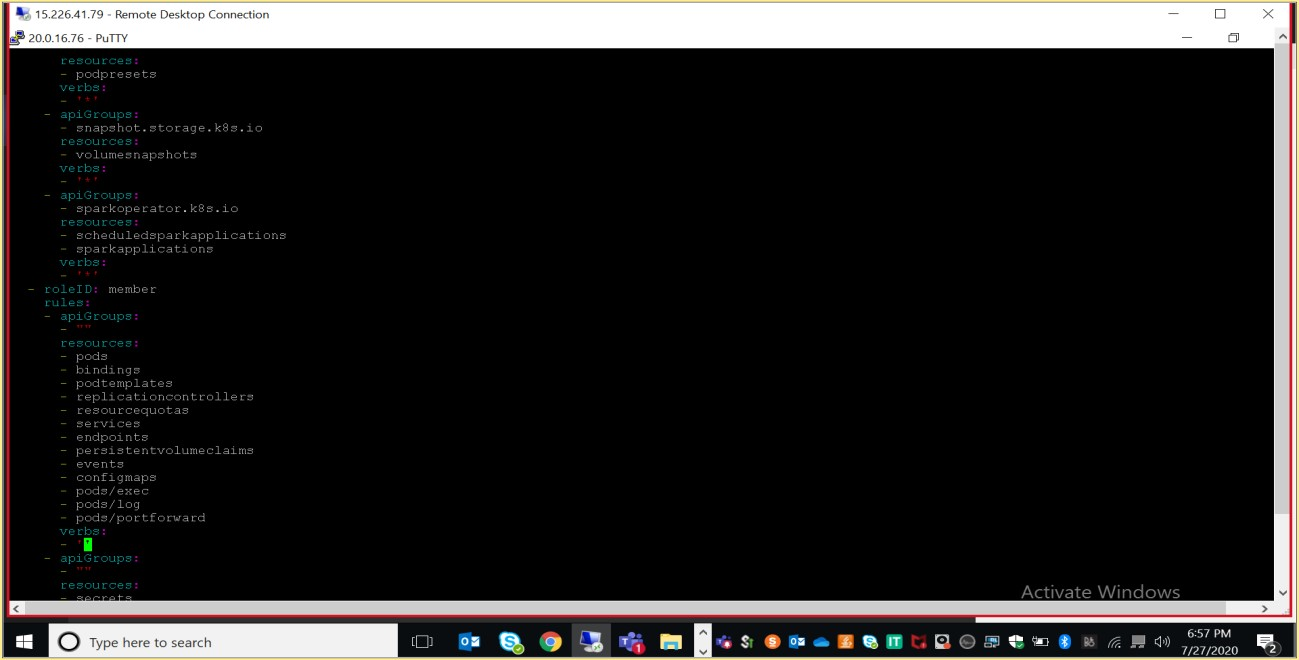
The following table lists the role specific acronyms that used within HPE Ezmeral Container Platform:
Below table describes HPE Ezmeral Container Platform roles and specific acronyms
| Acronym | Description |
|---|---|
| PLADMIN | PLADMIN stands for the Platform Administrator role. |
| KA | KA stands for the Kubernetes Tenant Administrator role. |
| KC | KC stands for the Kubernetes Cluster Administrator role. |
| KM. | KM stands for the Kubernetes Tenant Member (non-administrative) role. |
| TA | TA stands for the Big Data Tenant Administrator role. |
| TM | TM stands for the Big Data Tenant Member (non-administrative) role. |
| PA | PA stands for the AI/ML Project Administrator role. |
| PM | PM stands for the AI/ML Project Member (non-administrative) role. |
| SV | SV stands for the Site Viewer role. This is an internal role that is only visible to HPE Technical Support personnel. |
For more details on the specific functions that can be performed by the above roles refer to the Users and Roles (opens new window).
Creating Users:
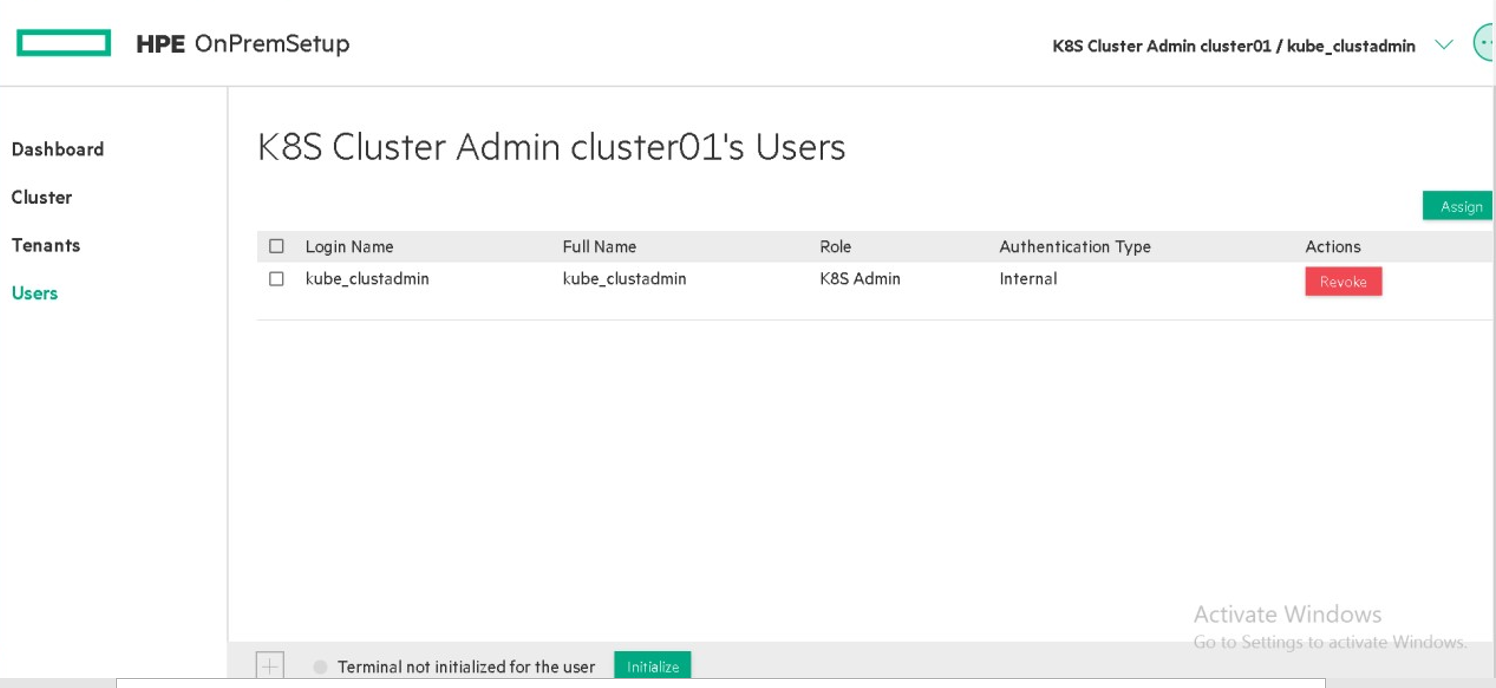
Only Platform/Site Administrator will have access to create users.User can be created as below:
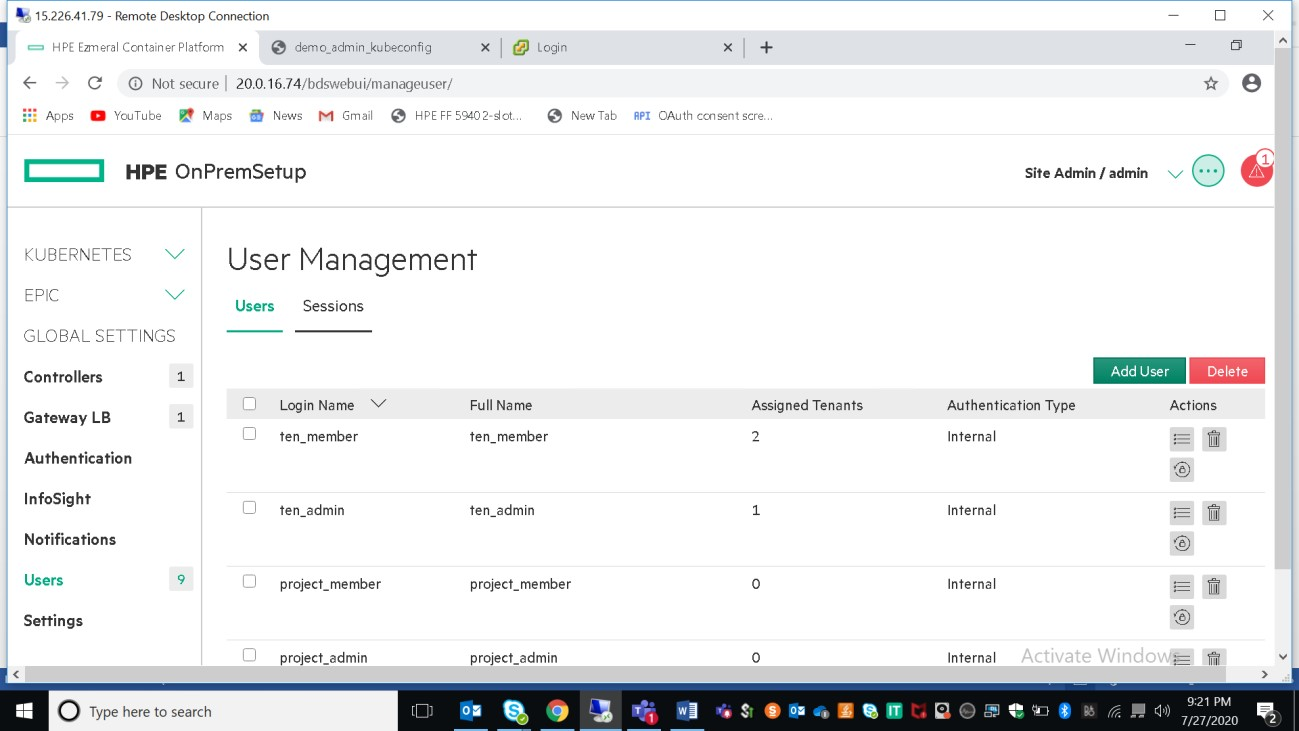
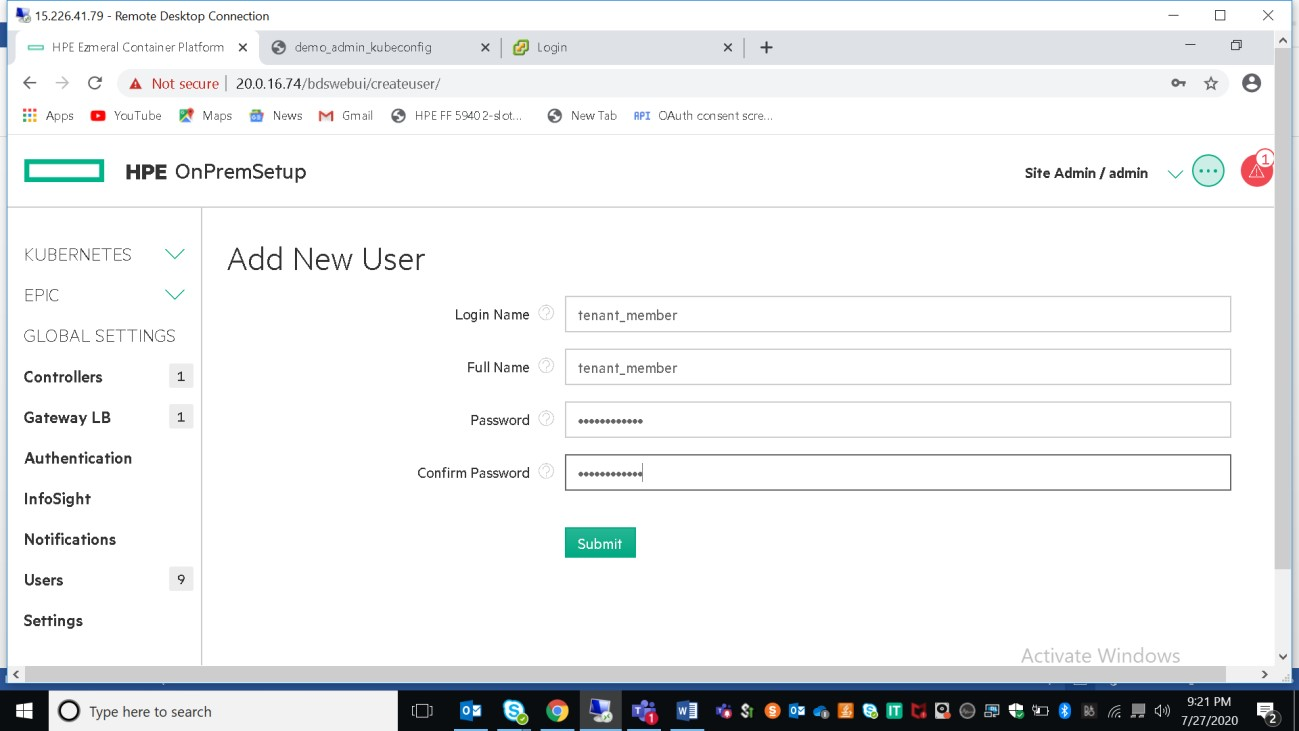
Once the user is created, edit the user to assign tenant/admin and roles. One user can be assigned to multiple tenants.
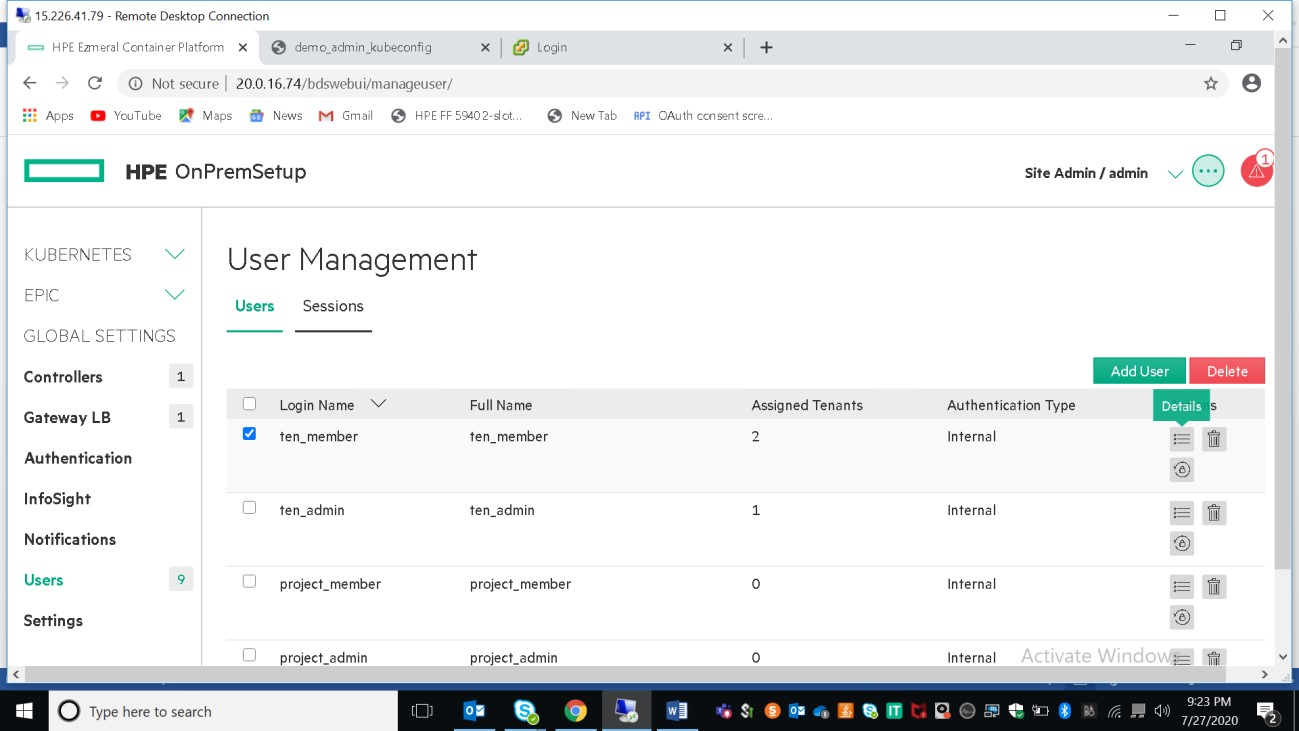
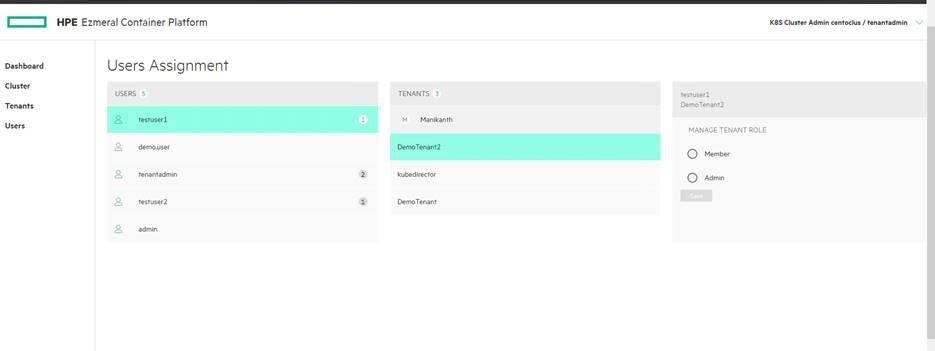
Each user must have access to at least one tenant. By default, Ezmeral HPE container platform provide support two roles those are admin and member. Users created with admin role has full rights to the associate tenant/project/cluster whereas users created with member role has limited access to the associate tenant.
NOTE
In this document only kubernetes users has been created. EPIC user details are not available.
User can revoke the access and no longer will not have access to the tenant.
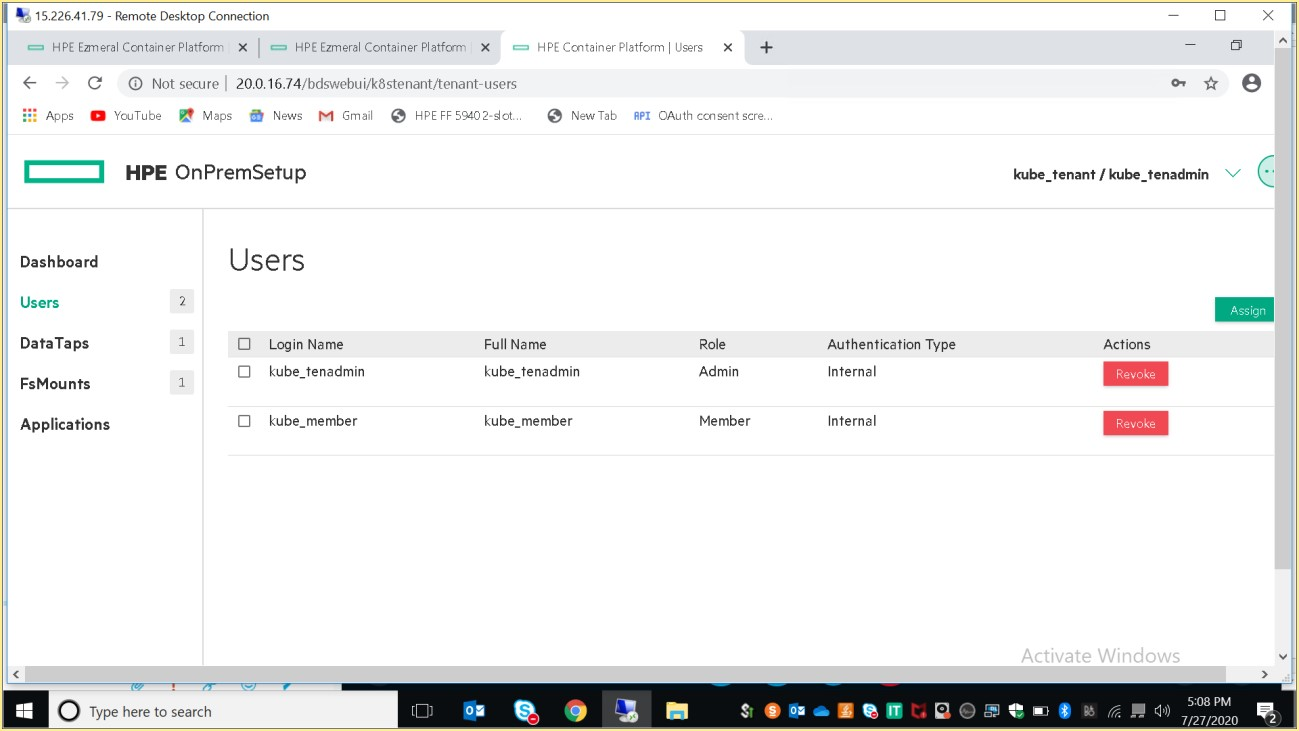
As part of invitation, following users has been created
Kubernetes Member Dashboard screen (see Dashboard - Kubernetes Member)
Kubernetes Cluster Administrator Dashboard screen (see Dashboard - Kubernetes Cluster Administrator)
Kubernetes Tenant Administrator Dashboard screen (see Dashboard - Kubernetes Tenant Administrator)
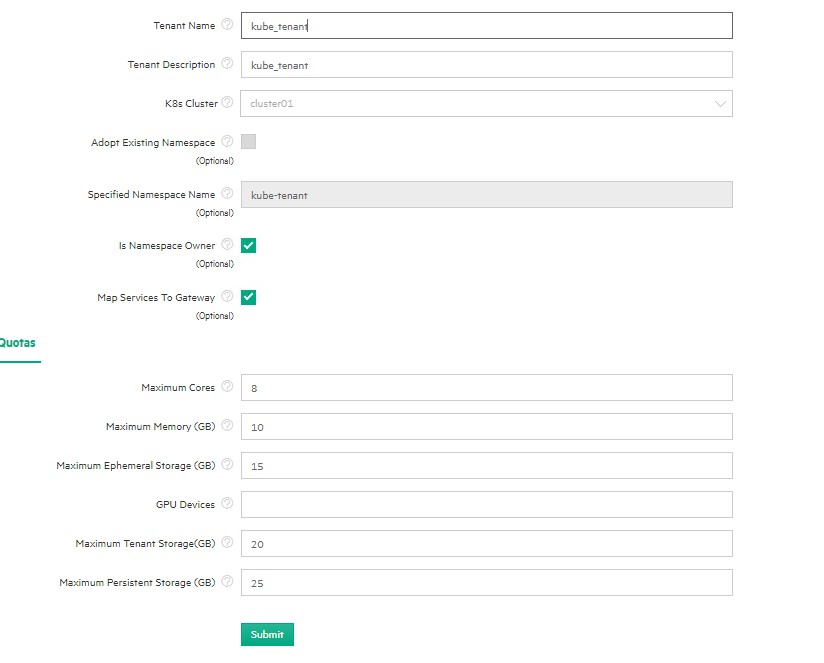
Creating Tenant: Created new tenant with name "kube-tenant" and assigned resources as below.
# Kubernetes Cluster Administrator
HPE Container Platform users who are logged into a Kubernetes tenant with the Cluster Administrator role can access the Kubernetes Tenant Administrator Dashboard screen by selecting Dashboard in the main menu.
The top of this screen has three buttons that allows you to download the plugins that you need to access Kubernetes pods within a cluster. The buttons are:
HPE Kubectl Plugin: Downloads the HPE installer for the kubectl command line tool for controlling a Kubernetes cluster. User will need to install this application.
Kubectl: Downloads the generic installed for the kubectl command line tool for controlling a Kubernetes cluster. User will need to install this application
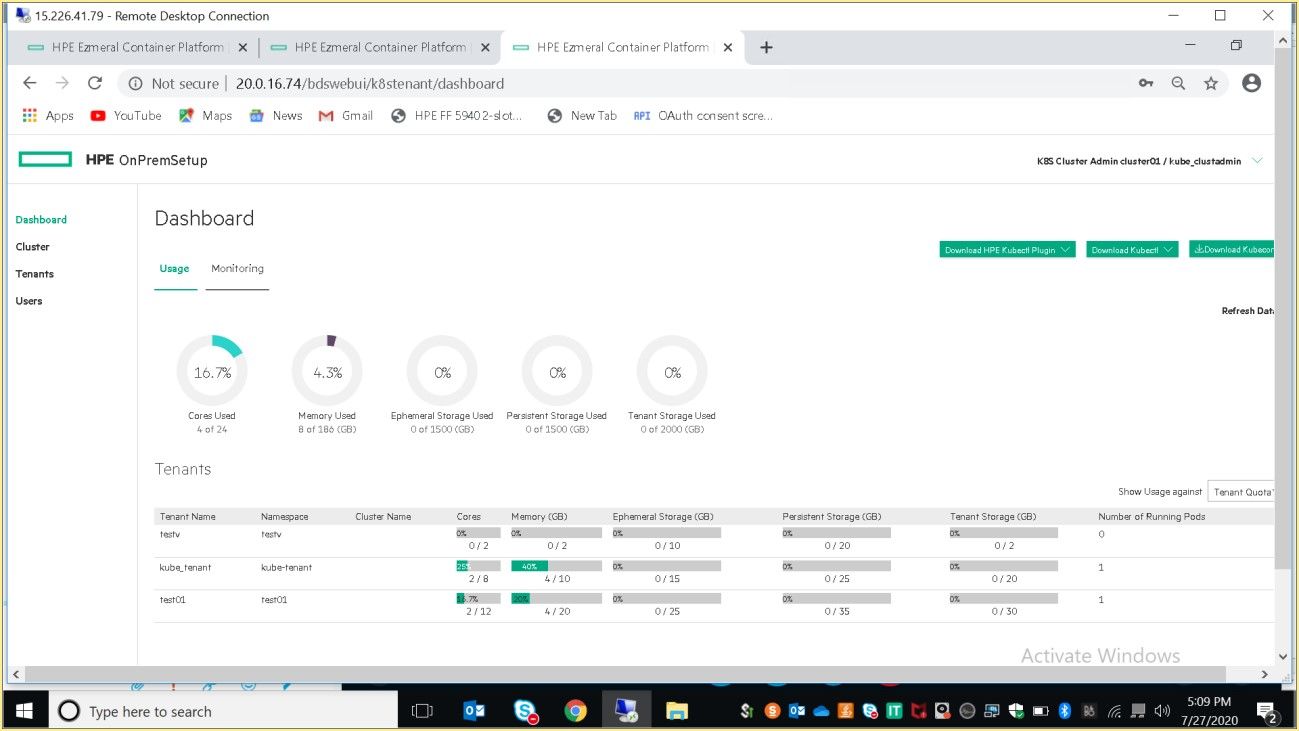
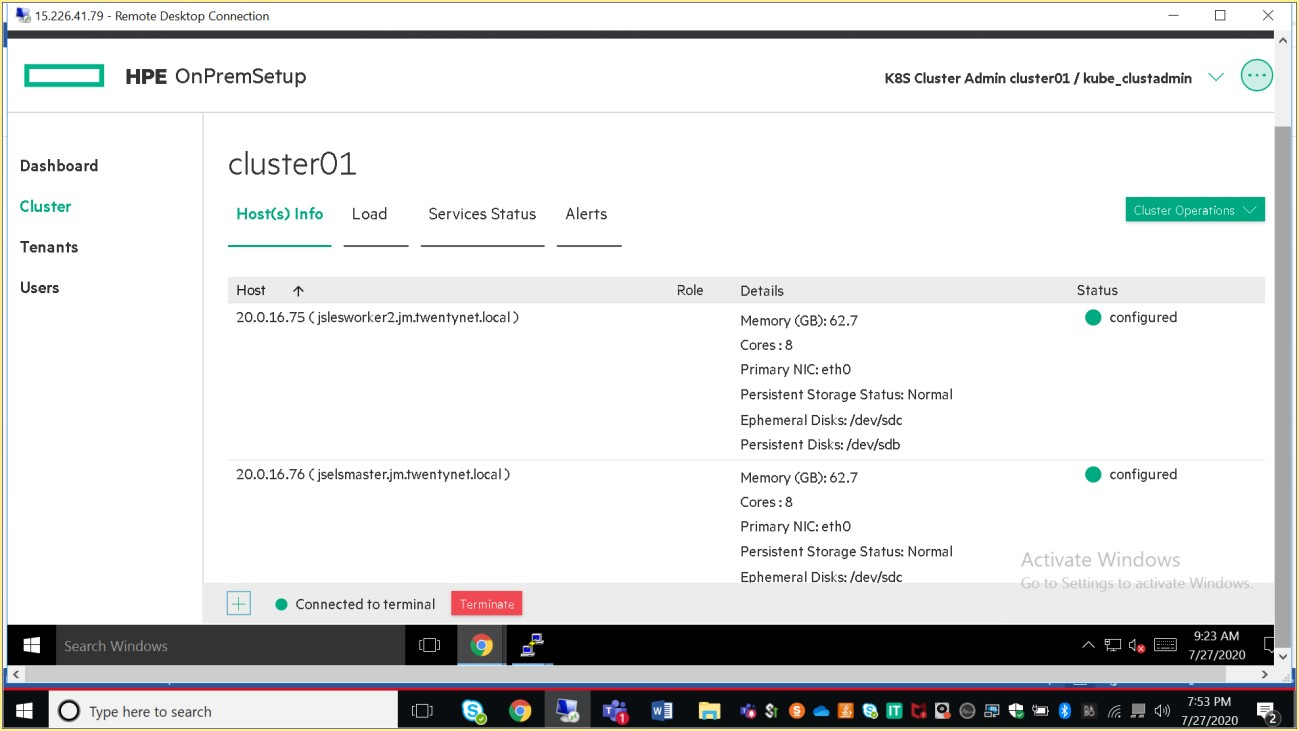
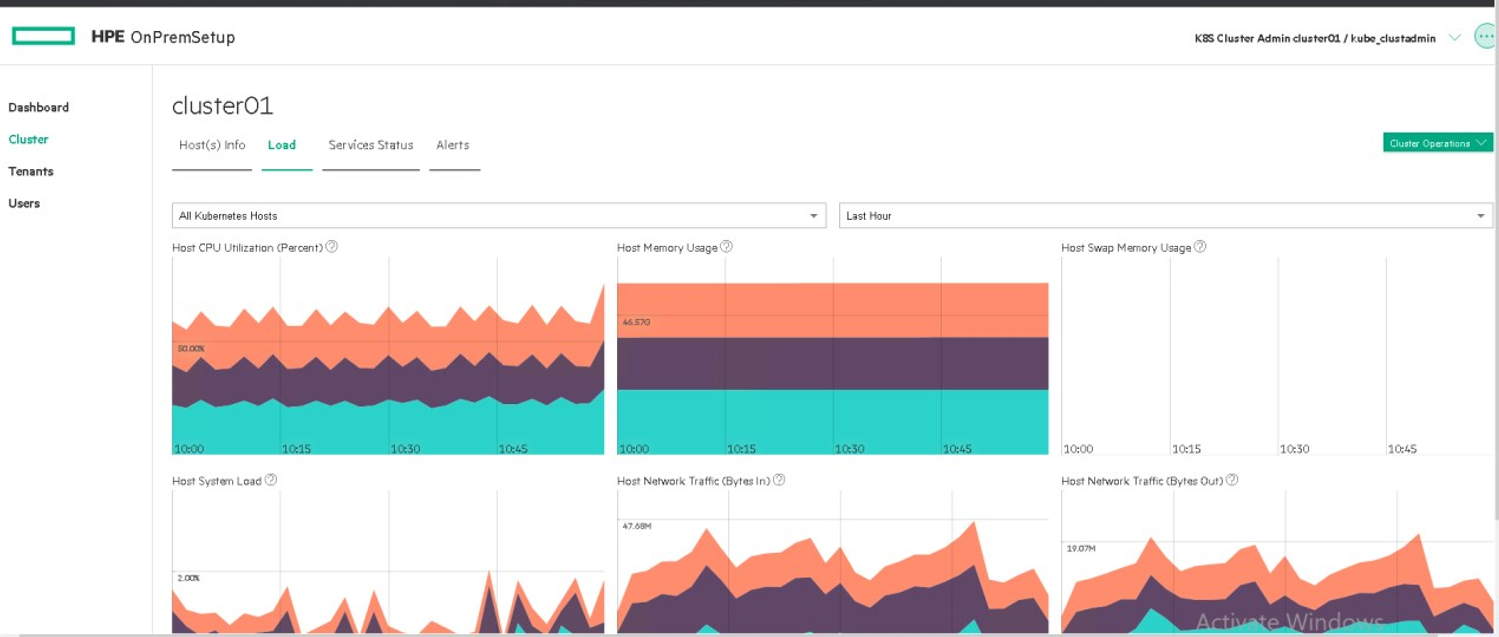

Admin user can have access to the kubernetes dashboard.
# Kubernetes Tenant Administrator
HPE Container Platform users who are logged into a Kubernetes tenant with the Tenant Administrator role can access the Kubernetes Tenant Administrator Dashboard screen by selecting Dashboard in the main menu.
Kubernetes Member:
HPE Container Platform users who are logged into a Kubernetes tenant with the Member role can access the Kubernetes Member Dashboard screen by selecting Dashboard in the main menu
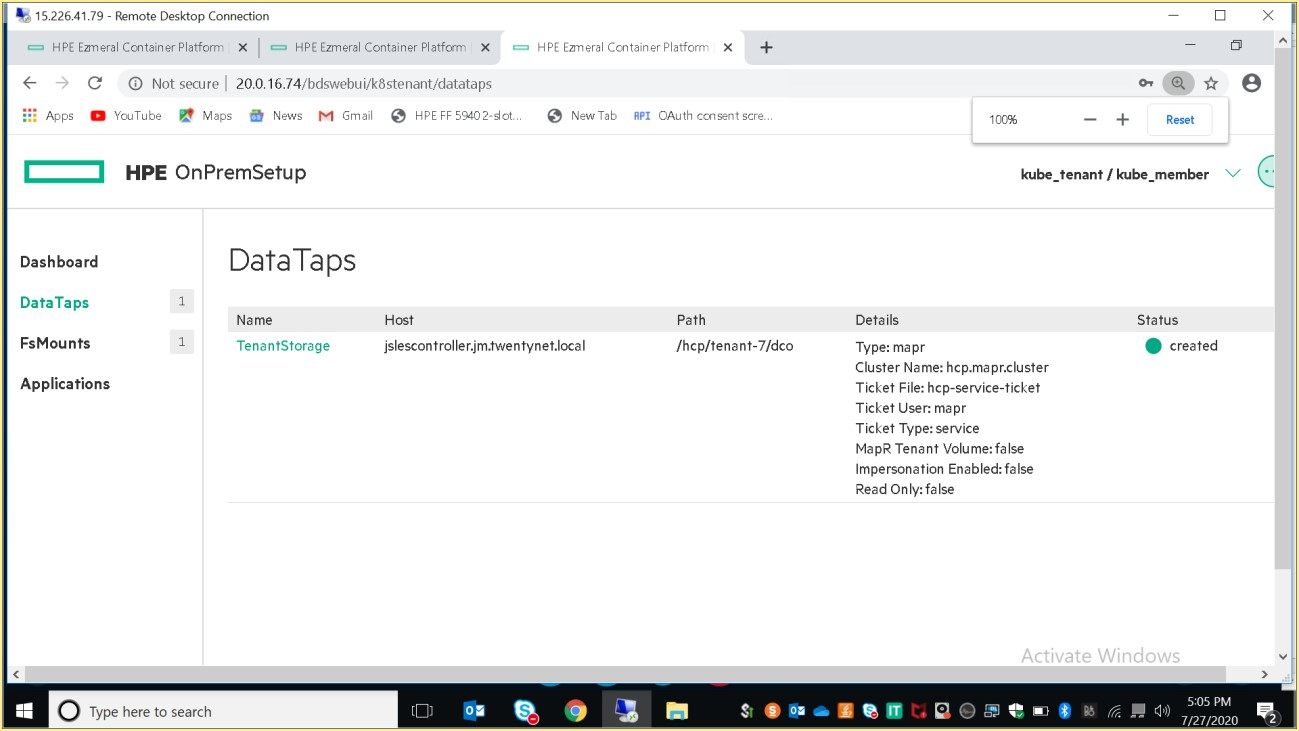
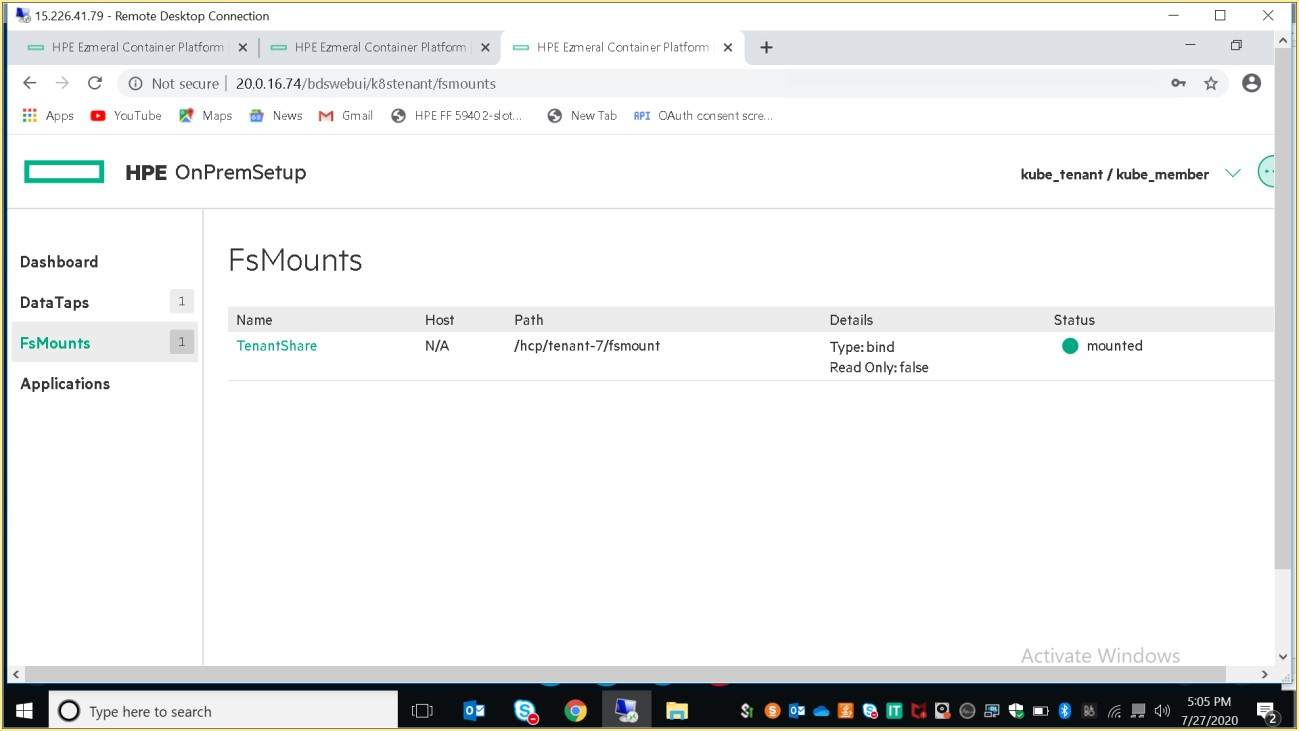
As mentioned previously, member would have limited access to the assigned tenant. For example: User cannot get information about resources like secrets, roles, role bindings.
Examples:
Command:
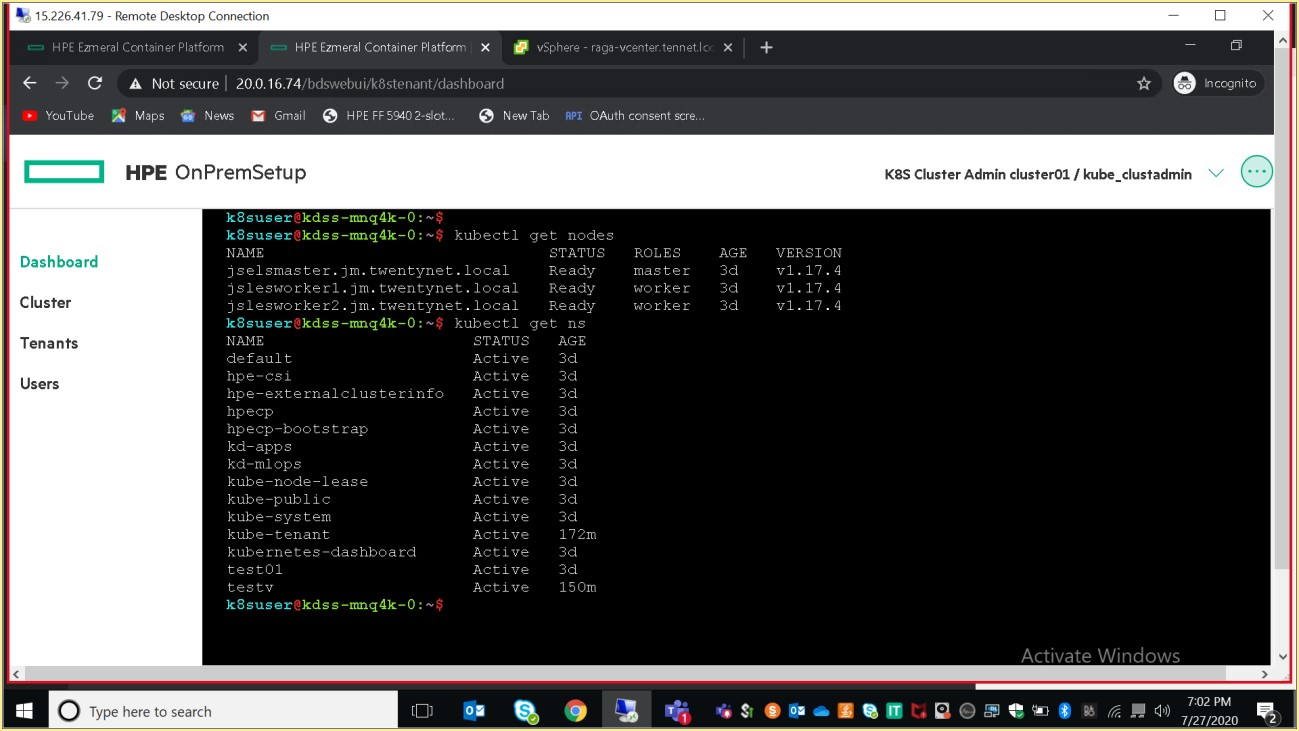
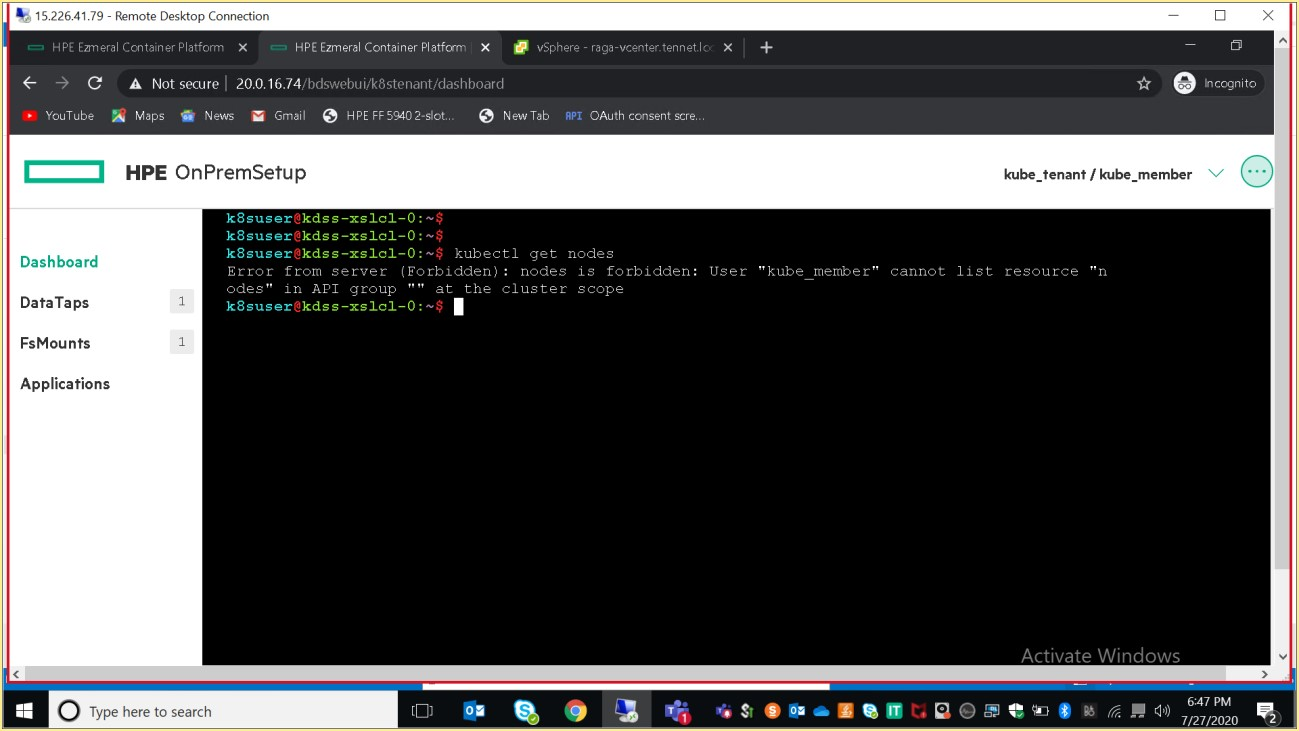
> kubectl get nodes
Description: This action is forbidden to the member
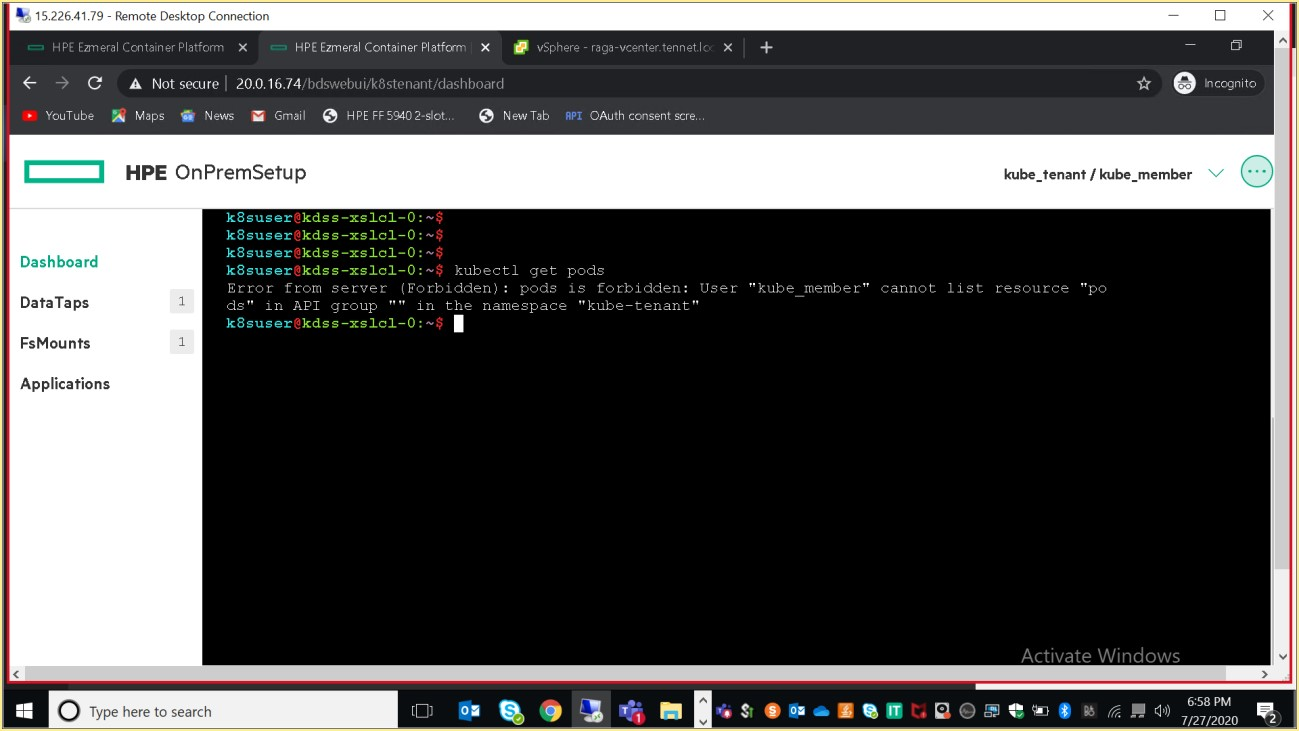
Example 2:
Initially, user does not have access to the "get" resource.
By executing following command kubectl edit hpecptenants.hpecp.hpe.com -n hpecp,Member resources can be modified. In this scenario, added get resources to the member user.
NOTE
Site admin/Platform Administrator can add the resources/grant access to the member user associated with specific tenants using following command.
> kubectl describe ns kube-tenant
> Kubectl edit --n hpecp hpecptenant hpecp-tenant-7